If you run a business - any kind of business - you should have basic information about data security. The data you process and store needs to have some kind of security in place. But when working with a large volume of data, depending on the sensitivity, the off-the-shelf data security solutions just don't cut it. In this article, we'll explore some of the reasons why you might need to implement a custom data security solution for your business.

Your data will be secure and accessible only by authorized personnel.
Data security is essential for any business - as your business grows and start holding a lot of information in your system, data security issues become more vulnerable, which is why companies offer custom solutions. By putting a custom-built data security system in place, you can ensure that only authorized personnel have access to it through robust security measures. Here are some of the major reasons:
- To protect your confidential information from being accessed by unauthorized users.
- To safeguard your systems from being compromised.
- To prevent sensitive data from being lost or stolen.
- To comply with government regulations and industry standards relating to data security.
- To ensure that your employees are properly trained in data security best practices.
Your business will be protected against hackers.
As you may be aware, all we can anticipate is that hackers continuously come up with new ways to exploit businesses and steal data. We are non-security experts, we never really know when our data will be abused next or how it will happen. Let me elaborate on this; here are some of the reasons.
The Methods They Use
Hackers use a variety of methods to gain access to your systems. We non-experts don't know what they are, but you must have heard some types of malware; viruses, ransomware, adware, Trojan, phishing scams, social engineering, etc. To protect your systems against these attacks, the best we can do is to rely on multiple anti-virus software that can update on a daily basis. Hackers continuously try to drop new bombs, and therefore your system needs to be continuously shielded in new ways.
Financial Damage
There are a variety of hackers who have different purposes. Most of them intend to make money fraudulently. They can gain access to personal data such as your bank detail, credit card numbers. Then they try to access your bank and credit card companies respectively, which can cause a financial damage to your business.
Financial institutions have their own tight security measures and most of the unauthorized access can be blocked. It means that the probability of the actual financial damage may be low. But stolen money from your bank can only be retrieved if you discover the unauthorized payment and report it to your bank. This involves unnecessary investigation procedures. It's best if your system can prevent any kind of hacking in the first place to mitigate unfavorable incidents.
Reputation Damage

Your data that hackers may steal is not restricted to your financial detail but your stakeholders' such as customers' and suppliers'. By accessing these various sets of data, they can trace all kinds of corporate secrets. This will lead to not just potential financial losses but also your reputation damage. The last thing you want as a business owner is any negative implication as a result of multiple harmful incidents. You may do nothing wrong, but the vulnerability of your system may make your business appear to be unreliable to your stakeholders. Even if nothing happens, by having a strong safeguard measure in place will build a good image of your business.
Any business that stores or transmits sensitive data needs to take data security seriously. While there are many software options on the market to help with this, advanced, customized security system designed especially for your IT system and accounting software can protect your business in a more effective way.
Customers will feel more confident doing business with a company that takes data security seriously.
Now you know when it comes to data security, businesses may have a lot to worry about not just to protect themselves but to protect their customers and prospects, suppliers, partners including affiliates. Between hackers and cybercriminals, there are many ways for information to be stolen or compromised.
So let's summarize once again why it’s important for businesses to take data security seriously by implementing custom data security protocols.
According to Statista, the biggest reason that average Americans worry about crimes is their personal financial information being stolen by computer hackers. 74% of the respondents to the survey said so. Whereas 33% of them worry about getting mugged and 22% of them worry about getting murdered.
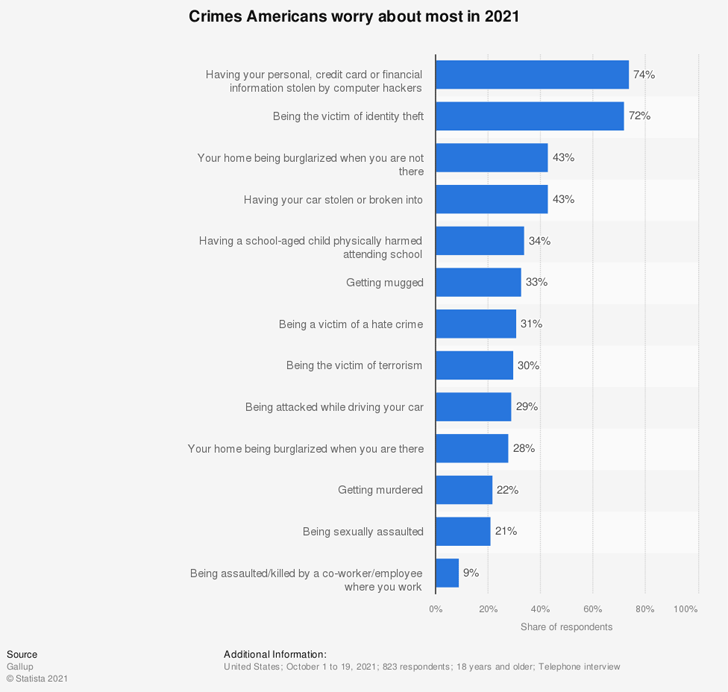
Looks like the statistics reflect the probability of the crimes today. We know that we can protect ourselves from getting physically harmed outside by not entering certain areas, not walking in the dark, etc. But we don't know if we are protecting ourselves while we are on the internet. When it comes to the online shopping experience, how do we make sure the company we are paying to is trustworthy? It is rather a business's responsibility to prove that its activities are in line with security regulations, so consumers trust the company.
Customer Confidence
One of the main reasons to implement custom data security is that it can help increase customer confidence in doing business with your company. Customers want to know that their information is safe and secure, and they will be more likely to do business with a company that takes data security seriously.
Protect from Cyber-Attacks
Another reason to implement custom data security is that it can help protect your company from cyber-attacks. Hackers are always looking for new ways to steal information, so it’s important to have strong defenses in place. Custom-made data confidentiality system can help you stay one step ahead of the hackers and protect your business from harm.
Ever-Changing Regulations
Finally, a tailored monitoring system can help you comply with ever-changing regulations and standards set by governing bodies. By complying with these standards, you can help ensure that your customers’ information is protected at all times.
Conclusion
Technology exists to make our lives easier and connect between B2C, B2B, and C2C. But where there's a connection made by technology, some will always attempt to break the chain with malicious intent. Things that are created by technology just cannot be monitored manually. As a business owner, your ultimate goal is to build a good reputation among users and continuously grow your revenue. Better safe than sorry, you should protect your IT infrastructure, no matter how small the scale of your venture may be.
